Ledgers are the primary ways settlements are recorded. The first double bookkeeping ledger system was recorded in use as far back as the 1300s. It is still the de-facto system used today to record transactions between entities.
Fast forward to 2008. Satoshi Nakamoto (pseudonym) was frustrated with the corruption due to the lack of transparency and centralized control of the traditional system. He proposed a transparent distributed ledger system that was immutable as a system of recording transactions. Thus Bitcoin was born.
But with all new systems, there is always room for improvements.
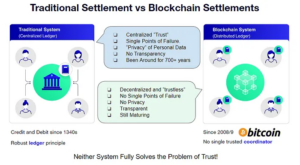
As discussed in our previous articles, full transparency does not solve the problem of building trust. In fact, privacy is a requirement in any trust relationship. For example, nobody would trust a credit card provider that revealed every purchase cardholders made just by someone having their credit card number. In a traditional blockchain space, every transaction is written in a public ledger. It would only require matching a wallet address to a name to see the full history of their transactions.
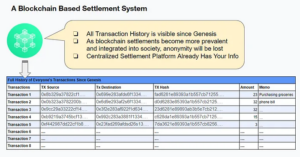
How can you have a blockchain that privatizes transactions and has enough flexibility to analyze and compute the data? Through integrating a proven technology into a scalable and interoperable blockchain.
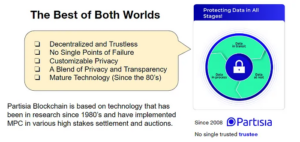
Developers can pick and choose which part of the data in the blockchain needs to be private and which can be public. All thanks to the Partisia Blockchain’s programmable MPC. A layer of governance can be enabled around the private data to allow for computation and access to select individuals. Those who access the data can also be audited transparently.
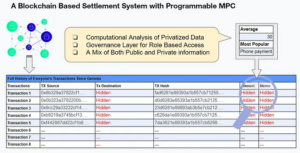
Now, even if someone has your credit card details, they will not be able to see your purchase history and your spending. If needed, a governance model can be created to ensure auditability and traceability to the system.
The importance is evident in our partnership with the International Committee of the Red Cross (ICRC). We partnered with the ICRC to build out a program for distributing aid through blockchain. One of their key requirements was privacy of the aid recipients. As they are a very unique organization, one of their key principles is in confidentiality and bilateral dialogue. The ICRC mainly operates in conflict zones and lack of privacy can mean life or death.

ICRC was able to solve their key challenge of privatizing the transactions of the stable tokens in the ecosystem thanks to Partisia Blockchain’s MPC. As shown above, the deposit of the funds from ICRC is kept private. As a result, transfers between the users are anonymous. To learn more, please watch our video of the overview of the solution here.
As blockchains become more prevalent, the need for privacy will continue to grow and take center stage. Various projects are already being built with private settlements in mind. We continue to speak with many organizations who prioritize the need for privacy in a blockchain solution.
For additional insights on this use case, come and watch our Q&A session we did on this topic.
By creating a programming language that allows for developers to use MPC in a generic way, Partisia Blockchain Foundation has made the creation of applications that can harness the power of MPC for different use cases a possibility. Partisia has been at the forefront of providing private MPC solutions since 2008. And by layering this technology on top of an interoperable and scalable blockchain, Partisia Blockchain is now paving the way for anyone to create solutions that can balance privacy and transparency to build trust.
To learn more about different use cases or partner with us for solutions, please visit partisiablockchain.com, check out our Medium articles, development documentations or email me at bruce.ahn@partisiablockchain.com.
In a traditional asset trading platform, front running is defined as the illegal practice of placing a trade based on advanced non-public knowledge of an upcoming trade which can impact prices. As shown in the example below, a broker can take advantage of a situation when he or she gets a large order by one of their clients. Since they know this order will impact the price of the asset, they place their own personal order ahead of their client’s order. Then, they place the client order, raising the stock price. Once this is done they will sell their own shares to profit off their clients order.
Another term used often is insider trading, which is based on a very similar practice of using information only they have access to in order to gain an unfair advantage over others.
In the Web3 space, everything is transparent and, ironically, revealing too much information can also create these situations. An example of this is front running on a decentralized exchange (dex) that you may have already heard of. This type of a front running is possible through the combination of having total transparency in the blockchain along with how Ethereum (and many other blockchains) prioritize transactions in a node’s mempool.
In this particular example, an attacker (usually a bot) scans the mempool to see a particular scenario that they can take advantage of. Scanning the mempool, they look for an opportunity to insert in a bid at a lower price but higher gas than another large bid already in the mempool.
Once their bid completes, they wait for the larger order to go through, raising the price of the asset. Then they place a sell order at a higher price than the buy order he placed ahead of the larger order, and pockets the difference. All this is happening in a blink of an eye, making it impossible for any normal person to be able to recognize they are being taken advantage of.
But what if we could make the orders private? This prevents the attacker from being able to read the auction details in the mempool, and making the bot unable to identify a situation to take advantage of.
Through multiparty computation (MPC), details can be kept private while still computing the winner. In the situation of this dex, the results of the prices are not revealed until the bids are completed, ensuring that attackers cannot gain any advantageous information ahead of time.
The team in Partisia has already provided solutions to solve this issue in multiple scenarios. From governments to OTC trading platforms, they have been trusted to run high stakes auctions in different levels and through enabling this technology on a blockchain, we are giving everyone the power to solve the problem of ensuring integrity in the bidding process.
For additional insights on this use case, we recommend viewing our Q&A session on this topic.
By creating a programming language that allows for developers to use MPC in a generic way, Partisia Blockchain Foundation has made the creation of applications that can harness the power of MPC for different use cases a possibility. Partisia has been at the forefront of providing private MPC solutions since 2008. And by layering this technology on top of an interoperable and scalable blockchain, Partisia Blockchain is now paving the way for anyone to create solutions that can balance privacy and transparency to build trust.
To learn more about different use cases or partner with us for solutions, please visit partisiablockchain.com, check out our Medium articles, development documentations or email me at bruce.ahn@partisiablockchain.com
Your opinion matters. It matters so much that the global online data market estimate is to be over US$270 billion dollars, all focused around buying and selling of your data to the highest bidders. It is a very complex web of transactions that ferry your data from one place to another and many times, your data is used in ways you never realized could be used for. From Cambridge Analytics’ controversial use of data to TikTok’s alleged aggressive data harvesting, there is a large market for your information and how it is used is very unclear.
The current Web2 market for surveys is in the exchange of your data. This means your opinion is collected, filtered, analyzed, sold and bought. The data may be collected anonymously, or it may be tied to your identity. Either way, this data is collected and managed by a centralized system, which has control over the data they purchased. There is also the ever growing concern of bots and AI scripts that automate and duplicate fake data leading to data integrity issues.

One of the ways a decentralized blockchain can help change the landscape of the survey market is through dissolving the centralized control problem. Because the data can be made public, and with no single point of control of the data, you can be sure that the data can reside on-chain and has no central ownership or control. However, this can create problems with privacy. All data is now public and this creates two issues.
A unified public and private smart contract, like the one Partisia Blockchain supports, enables the best of both worlds and solves the two issues above, where you now have a decentralized blockchain that eliminates any controlling entity while still being able to privatize your data. Not only does this retain the data marketplace but redefines it in a way where the user now has control over the data.

The online survey industry is large and is continuously growing. And this is because surveys hold a lot of valuable data. As reviewed in our earlier article on privatized voting, we use multiparty computation (MPC) on the blockchain to hide your data on-chain, but still allow for computing of the data.

While the private voting use case reviewed a very simple computation on who the winner of an election was, Partisia Blockchain’s programming language allows full algebraic equations to be used to calculate any number of computations using the hidden data. This means not only being able to compute on a single category, but also combine results of the computation from multiple categories.

This change in privacy of your survey data creates a new change in how the data marketplace can be viewed. By allowing the survey participants ownership of their data, but still allowing for the computation of it, the marketplace of the data has now shifted from buying and selling of your data to buying and selling of the “use of your data”. You now still hold ownership of the data and you are now selling the use of your data while still keeping your data private. This paradigm shift creates new opportunities for a different marketplace where you are not just selling your data one time, but rather allow for the possibility of both updating of the data in real time as well as being rewarded each time your data is used. And through privatized authentication, the data quality improves as well leading to better accurate analysis.

For additional insights on this use case, we recommend viewing our Q&A session.
By creating a programming language that allows for developers to use MPC in a generic way, Partisia Blockchain has made the creation of applications that can harness the power of MPC for different use cases a possibility. Partisia has been at the forefront of providing private MPC solutions since 2008. And by layering this technology on top of an interoperable and scalable blockchain, Partisia Blockchain is now paving the way for anyone to create solutions that can balance privacy and transparency to build trust.
To learn more about different use cases or partner with us for solutions, please visit partisiablockchain.com, check out our Medium articles, development documentations or email us at build@partisiablockchain.com.